In between the waves of Petya Ransomware-wiper, another serious ransomware were spreading across, The “Karo Ransomware”. The initial vector being spam mails with a document file.
The document file is password protected and this malware is Virtualization aware and refuses to run in sandboxes.
Once infected Karo encrypts the files with the (.ipygh) extension and it will communicate with the TOR Command and communication server.

Lets Jump in..
One of the spam mail originated from an e-mail address “johnitgbwp[at]outlook.com”

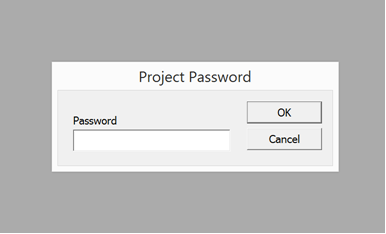
Once the user tries to open the document, a password popup will appear to enter the password which is in the body of email. This is a common trick used my offenders to evade the automated analysis and sandboxes.

Once the password is provided, the document opens and seeks the macro to be enabled to run the VB code.

When we try to analyse the macro code with in the document, another protection is implemented by the offender, may be to stop the analysts or anyone from peeking the code.
Once this protection is bypassed, we will be able to see the actual VBScript which is embedded in the user form

The VBScript is invoking the PowerShell to download and before execution the code will do a PING to 127.0.0.1 for 15 times, then the payload will be executed in the temp folder of the victim machine. (Common way used by offenders these days)
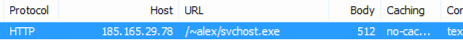
Now let us analyze the executable which the script downloaded “svchost.exe”

This executable was found to be smart assembly obfuscated, mainly to make reverse engineers sweat.

Now, Ya! We need to sit sometime to figure it out. As an analyst, you may skip the static analysis and go ahead with dynamic alone. But here comes the trick, when you execute this malware inside a Virtual Machine, it will not exhibit its actual activities, because it detects the virtualization. Now we know what is the importance of Code Analysis while performing analysis.
Now, Let’s see what’s in it. Once the execution starts, the malware will check whether it is being executed in a virtual environment or not. This will make sure the malware is not being analysed by reverse engineers or any sandboxes.

The below snippet of code is from the source of the executable derived after de-obfuscation and modification.

The code segment queries the system information, and checks for the keyword “virtual” or “vmware” or “virtualbox”. For example, let us assume VMware, the fields of interest are:
System Manufacturer: VMware, Inc.
System Model: VMware Virtual Platform
Thus above virtualization check by malware will easily identify that it is being running inside a virtual environment.
Now what will happen if it detects that it is being executed in a virtual environment?
The malware will follow a separate routine which will run “C:\windows\system32\cmd.exe” with “/c PING -n 5 127.0.0.1 & del /f /q “%temp%\*.*” parameters. As we can see these parameters are base64encoded within the executable.
Throughout the malware code, the important parameters are base 64 encoded.
The invoked command will do a PING to 127.0.0.1 for 5 times and will exit, after deleting all the files in the temp folder of the machine.
Otherwise..
The executable code will progress with infection its routine. For that, we need to trick the malware or patch it. I did a small tweak and made malware to run its actual infection routine within the VM box, bypassing the above mentioned “clean the trace” routine.
Once the infection routine starts, malware will copy itself as “svchost.exe” at “C:\Users\<username>\AppData\Roaming”. Then a shortcut file with name “Notepad.lnk” is created pointing to the copied executable and will be saved in the startup folder, as a persistence mechanism.


We can see that malware creating a mutex named “MyUniqueMutexName”

Then the malware queries and enumerates the logical drives in the machine.
A file is created and dropped at “C:\Users\<username>\AppData\Roaming” with name “aes” ( 32 characters are written randomly generated from seed). This file is then made hidden and once infection completes, it’s deleted.




Meanwhile, the malware is checking whether any file named “svchost.exe” is there in the directory “C:\Users\<username>\AppData\Roaming”, and if so, it will delete it and then will copy the malicious executable to the directory with name “svchost.exe” . This svchost.exe is used for persistence via earlier created “notepad.lnk” in startup folder.

If no files named “svchost.exe” is found, malware will copy itself in the directory as “svchost.exe”

Now, malware will check if any folder “Tor” exists in %temp% folder and if not, it will check if any process named “Microsoft.vshub.32” in the victim machine. If it is running out there, the malware will kill it.
The reason, we will come to know shortly.

Next the malware will download the Tor browser package from:
“aHR0cHM6Ly9kaXN0LnRvcnByb2plY3Qub3JnL3RvcmJyb3dzZXIvNy4wLjEvdG9yLXdpbjMyLTAuMy4wLjguemlw”
Wondering what it is? Ya it’s the base64encoded URL to download tor package
It decodes to below URL:
https://dist.torproject.org/torbrowser/7.0.1/tor-win32-0.3.0.8.zip

This downloaded zip package is saved at %temp% folder with a 5 character randomly generated name:


Random Name Generator is used for generating the 5 character and the method used is shown above.
Then this zip package is unzipped and immediately the zip archive is deleted. Then the malware will write the required configurations for tor connectivity in the “torrc” file:

The parameters are base64decoded, and written in the torrc file :

The “tor.exe” file in the Tor directory is renamed to “Microsoft.vshub.32.exe”. Then Tor directory is moved in temp folder out of the “randomly named parent directory” and the parent directory is deleted.

The %temp% directory is given Full permission to itself and sub-directories by calling “icacls” command via “C:\windows\system32\cmd.exe” (base64encoded).

Now the “tor.exe” which is renamed to “Microsoft.vshub.32.exe” will be executed with parameter “–f ./torrc”. Also a sock listener and control listener is opened . That is why earlier malware checked for any process in name “Microsoft.vshub.32.exe”. Malware needs to run smoothly without conflicts 😉


Just if we try to recreate:

Now with the tor environment setup, the malware is trying to communicate with an .onion domain, carrying the information like username, Operating system, Machine name details.

Next the malware is trying to communicate with below URL


The “aes” field now contains the base64encoded strings ( including the RSA 2048 encrypted byte values of the RNG generated strings which the malware generated in the beginning).

After this stage, the malware kills the below processes:
/c taskkill.exe /f /im MSExchange*
/c taskkill.exe /f /im sqlserver.exe
/c taskkill.exe /f /im sqlwriter.exe
/c taskkill.exe /f /im mysqld.exe
Then starts the encryption process . The malware will search across the machine, for the file extensions and will be compared with set of extensions list. If it is not “.ipygh” and matches any of the extensions in the set, those files are encrypted.

As we can see, AES256 encryption algorithm is utilised,by using the file extensions and then the encrypted files are appended with the extension “.ipygh” .
Same information is mentioned by phishlabs here about the encryption “Karo, coded in .NET, uses the on-board RijndaelManaged class to encrypt files” . That sample consisted 21 extensions, but in our sample its 12 .


Then again the malware will communicate with same onion URL with information after encryption, may be information regarding objects encrypted (not sure) :

Once the encryption and command and control communication happens, the malware will extract a “karo.Readme.html” from its resources. This file is extracted from the resources and saved as “readme.html” at the desktop of the victim machine and executes it.


Once we navigate to the generated onion website, we will be able to see few ransom notes including payment information, bitcoin wallet, and date, time before we should pay the ransom amount.

Immediately, the malware will download an image from “hxxp://ibvmcu4eayyxjc4j.onion/wall.png”. Then it will be opened as ransomware desktop wallpaper after saving it as .jpg file at %temp%.
After all the above mentioned stages, Finally, the malware delete its traces and kill the running process after invoking “cmd.exe”.
- /c taskkill.exe /f /im Microsoft.vshub.32.exe.*
- /c PING -n 5 127.0.0.1 & del /f /q “%temp%\*.*”
- Deletes “aes” file in the Appdata folder.



After encryption of files:

Once we simply navigate to the .onion command and control server, we can see as below:

It is an executable which will again show the steps to pay and buy the decryption tool:


Conclusion
We have seen lot of very dangerous campaigns these days, including wannacry, Petya Wiper, Loki Bot , Karo Ransomware. The first two used very critical vulnerabilities which got leaked from NSA, may be because of that lot of concentration was on those threats. Being said that, between those threat waves, Are we missing some dangerous threats?. For example, when Petya Ransomware was in top news, we could see lot of IOCs being spread claiming its Petya Ransomware IOCs. But actual fact was those were mixture of IOCs related to Petya, Loki and Karo. But anyways, IOCs are always juicy and important even if it is mixed up or not.
That said, Karo Ransomware was playing hide and seek behind the “Petya” Waves, yet it is indeed very dangerous.
Indicators Of Compromise (IOC):
Document files:
EF925730F827406A8E54BA054131466D8B99596A79C3BA57E088EE65B413FBF6
D6EEEED2C2668835D4C7D0EEDA7A0AB9D906E9BD7889A2EC136D5FE95E394C31
D91804512E2439A0BF9000F6E639A7950E60E408CECF5D556E0724F324B3964B
B1BD79A9EF9E7AF36DDDAC60D7D2C7A48E211F4D958590DB759E49D1CD89F862
7BD82E5A51D5119A1D2E0221AFC589D4AAB2B27ED42AB4D6C0EEAA6E0F913E45
0D3C41A5413C0898977C806A33EEB69FCC2D7033B6A36DB00F92361EED06661D
881698EC21214B5656F46DAD4D24B86343197D0745A3B742F9FEC0002B38E3AA
FCE5F59B86AC144A0D82CB8F9FFEC09F457281B96DACAC8FBCD501CF7301AD1D
5E5403197E65834CB17C66448C7B853426665C5A895AA44AA0F72A02EFCCE38C
59E4E01C4B93AEE63A93A3C5FA76C34428B8580731AADB7038728EBFCB54B486
A8551A41F6BAEAF14B31A5597940A95949197F250B308CDCF3DD4A0D3780BEC3
5D1FB5199BD54D4512EA5A8C62DE7E3FE840B79F9B973EA2E7C76CFE931389B2
20201552059CD40DA33951C8B0416385DC5053D980FFB20CF079B36D923DA96F
01779235048F0F029195D2D4B08878E929F348EE6BF771BD7443E6ACEFFCBDB9
BDB33B923715AC20A0B46629DF32C613310BBDA3BB2F49533B5701D86F32A2D7
8E6B0D33EF324476416C43468EB5A17EA62F209C2A4F30FB4F8FE54069DEE50F
1EC5A0AB3A458D2B45D15C4482049F462C668F5712DE7482D7706A88E5E90C60
198F77E10ABED9CA7C395C81CF571D546AF88CB6DD2B6FBCAB4B9EBA746AEE52
4128943162FE8977CA1047583F471EF728ACBE34A4FE3A4CA63227982154421D
A94A6F2B9E974FFE56ED9DE41C065E27FF4B525081A54683A3BE90694282AF87
05C1C3AC0D55C64DE4A37DA1D90D1C71F2E176A26295EC587F35B6346559722A
E69D940DAB60B6A2F7D4E8B76D58C4F6BD1E6F0692A06B0B294C564467909AB2
6B2048775B1AEC9BD2506090D5BF79AC9CFCC61D01D21729BAF0A8CD1542F277
F56F033E3E24CFF1D6FA5ECBB8F36D92A27D7CD01A32793791BE7E93F4ED5B2C
189622F5C2AAC841C03330549A356748542D898039AFDC1FD33F2033E0258AA9
0EAC6E0FDF8C17A485AE322C23BBCBEE6A22ECC86DD562338D6F608A4E4ABEA4
9D571111085C006B23CBCEC8107392B4954944BD865517E3EC6075D94C7F3816
B52B6CF2F67672D9767217ADC1C2D6D1BD34AE2AC1C8FE9B2EDBC5AC68682477
Executable
Location: AppData\Roaming\svchost.exe
E9ADA9381BAD87750FE25CA24380AAAB1E358D88BC002C58936B00B5E31AB211
2DDF8DF2EE880DAE54A7F52E4BF56F896BB3F873FB6B8FDB60CAE4A3DE16FF49
7F081859AE2B9B59F014669233473921F1CAC755F6C6BBD5DCDD3FAFBE710000
3E896599851231D11C06EE3F5F9677436850D3E7D745530F0A46F712E37CE082
0C9FA52ACE8019B43C91F4859ECDDFDE6705141B9283FEF05C6C4C37A5C1777A
D9B05EEC2CEE806DDBE6BF8642A61FF493AC9D9D63967CEC749C0F169AACBB01
21E1BC4340221FBCCEE28D59333C20B20755E34E2F3391B90837172BD07FBF01
F0CFECAAD9777808B511DF566E7ADF7FC58CA649011CB8F53094891C38E73239
E9ADA9381BAD87750FE25CA24380AAAB1E358D88BC002C58936B00B5E31AB211
3D876874C7ECC0FE43878B25879AE519911AEFE95CE0E0F2220DE22E90CA9524
71F52862CDF708CA203BD07836838FDD41E51473ADDFF1D0B004D8467281BB21
E742597C2C5C1F7F246F18FB10C1B29900456C1EDDC3C3EDE6F3325B409D7537
E5C643F1D8ECC0FD739D0BBE4A1C6C7DE2601D86AB0FFF74FD89C40908654BE5
Folders Added:
C:\Users\WIN\AppData\Local\Temp\Tor
C:\Users\WIN\AppData\Roaming\tor
Files Added:
C:\Users\WIN\AppData\Roaming\svchost.exe
C:\Users\WIN\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\Notepad.lnk
C:\Users\WIN\Desktop\ReadMe.html
C:\Users\WIN\AppData\Local\Temp\Tor\libeay32.dll
C:\Users\WIN\AppData\Local\Temp\Tor\libevent-2-0-5.dll
C:\Users\WIN\AppData\Local\Temp\Tor\libevent_core-2-0-5.dll
C:\Users\WIN\AppData\Local\Temp\Tor\libevent_extra-2-0-5.dll
C:\Users\WIN\AppData\Local\Temp\Tor\libgcc_s_sjlj-1.dll
C:\Users\WIN\AppData\Local\Temp\Tor\libssp-0.dll
C:\Users\WIN\AppData\Local\Temp\Tor\Microsoft.vshub.32.exe
C:\Users\WIN\AppData\Local\Temp\Tor\ssleay32.dll
C:\Users\WIN\AppData\Local\Temp\Tor\tor-gencert.exe
C:\Users\WIN\AppData\Local\Temp\Tor\torrc
C:\Users\WIN\AppData\Local\Temp\Tor\zlib1.dll
NETWORK ACTIVITY:
185.165.29[.]78/~alex/svchost.exe
ibvmcu4eayyxjc4j.onion
rvdhwkyrin7[.]net
dlyfr46r6[.]com
zt2wahvphwrw[.]net
5qdbxgpqub[.]net
mxleilypb67h[.]com
rvdhwkyrin7[.]net
rsbynyj7233fmkwylfht[.]com
5qdbxgpqub[.]net
107.170.101[.]39
86.59.21[.]38
199.254.238.53
171.25.193[.]9
194.109.206[.]212
131.188.40[.]189
154.35.175[.]225
178.140.104[.]18
192.99.45[.]229
185.96.88[.]29
86.105.212[.]130
144.76.163[.]93
151.80.42[.]103
193.23.244[.]244
198.96.155[.]3
5.39.78[.]101
62.210.123[.]24
72.14.188[.]52
79.172.204[.]36
82.195.75[.]101
93.186.200[.]213
Recommendation
- End-user awareness program should be replayed periodically
- Strict Back process should be maintained, which is very helpful in scenario of Ransomware infections
- Disable macros from MS Office files using Active Directory Group Policy
- A well defined patch or Vulnerability management process should be maintained
- Strict and useful policies should be implemented at inbound spam/malware protection
- Regularly update the AV signatures and other controls
- It is highly recommended to disallow execution of any files in %temp% folder via endpoint policies
Reference
https://info.phishlabs.com/blog/not-notpetya-an-analysis-of-karo-ransomware
https://www.bleepingcomputer.com/news/security/the-week-in-ransomware-june-30th-2017-notpetya/